Encrypting passwords using
Ansible Vault
You are not happy about having your passwords sitting in the clear inside your Ansible files; you really would like these files to be encrypted. Ansible has a nice feature called Vault that allows you to accomplish this.
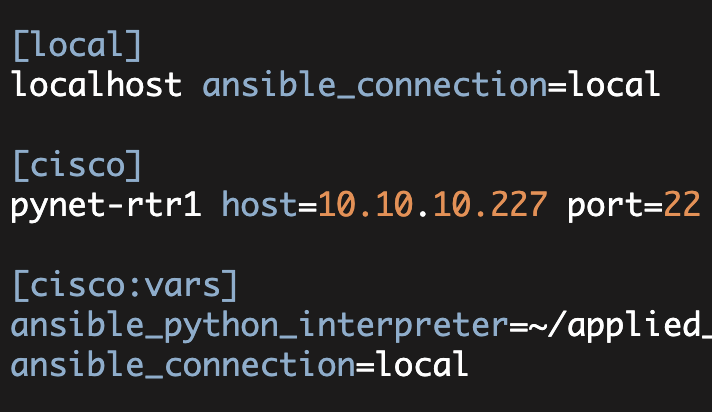
Take, for example, the following scenario—you have four Arista switches and a single Juniper SRX:
[local]
localhost ansible_connection=local
[arista]
pynet-sw1 eapi_port=8243
pynet-sw2 eapi_port=8343
pynet-sw3 eapi_port=8443
pynet-sw4 eapi_port=8543
[juniper]
pynet-sf-srxThe above file is my Ansible inventory file which I have relocated to ~/ansible-hosts.
Now Ansible has a lot of ways to specify host and group variables. One of these methods utilizes a directory named 'group_vars'. By default, Ansible will look for the 'group_vars' directory in the directory containing your inventory file.
Inside of this group_vars directory you can create a subdirectory named after each of the groups:
$ cd group_vars/
$ ls -al
total 4
drwxrwxr-x. 4 kbyers kbyers 33 Mar 30 13:31 .
drwx------. 26 kbyers kbyers 4096 Mar 30 13:32 ..
drwxrwxr-x. 2 kbyers kbyers 45 Mar 30 13:33 arista
drwxrwxr-x. 2 kbyers kbyers 45 Mar 30 13:31 juniperEach of the files inside of these 'group' directories will be processed looking for variables relevant to that group. So inside of the 'arista' subdirectory, I can create a standard.yml file and specify the following variables:
[ group_vars]$ cd arista/
$ cat standard.yml
---
ansible_connection: local
eapi_hostname: 10.10.10.10
eapi_username: admin
eapi_password: arista123I can create a similar file inside of the ~/group_vars/juniper directory.
At this point, I can execute a test playbook. This playbook adds a VLAN onto the four Arista switches (this verifies that my Arista inventory definition including group_vars/arista/standard.yml is correct):
$ ansible-playbook create_vlans.yml
PLAY [Arista-Ansible Exercise1] ***********************************************
GATHERING FACTS ***************************************************************
ok: [pynet-sw1]
ok: [pynet-sw2]
ok: [pynet-sw3]
ok: [pynet-sw4]
TASK: [create VLANs] **********************************************************
changed: [pynet-sw3] => (item={'vlan_name': 'kb5', 'vlan_id': 225})
changed: [pynet-sw1] => (item={'vlan_name': 'kb5', 'vlan_id': 225})
changed: [pynet-sw2] => (item={'vlan_name': 'kb5', 'vlan_id': 225})
changed: [pynet-sw4] => (item={'vlan_name': 'kb5', 'vlan_id': 225})
PLAY RECAP ********************************************************************
pynet-sw1 : ok=2 changed=1 unreachable=0 failed=0
pynet-sw2 : ok=2 changed=1 unreachable=0 failed=0
pynet-sw3 : ok=2 changed=1 unreachable=0 failed=0
pynet-sw4 : ok=2 changed=1 unreachable=0 failed=0Now this is all fine and good, but the password is still in the standard.yml file in the clear.
Now let's move the password out of standard.yml and put it into the ~/group_vars/arista/passwords.yml file:
$ cat passwords.yml
---
eapi_password: arista123Now I can use the 'ansible-vault' command to encrypt the passwords.yml file:
$ ansible-vault encrypt passwords.yml
Vault password: # specify a vault password to use
Confirm Vault password:
Encryption successful
$ cat passwords.yml
$ANSIBLE_VAULT;1.1;AES256
37633932346233383134646133636236373430623961623530383935323730359965
3634366238323939366130086431393864663630383432380a673265393334317439
63363430373138666435373439393865333138623630343064653833323730363233
3431626133393838370a326938653039319991633866353237666333333061306539
31336562388437376536303939663862823126623063643964396232303866613038Now, when I try to execute my Ansible playbook, I receive the following:
$ ansible-playbook create_vlans.yml
ERROR: A vault password must be specified to decrypt /home/kbyers/group_vars/arista/passwords.ymlI then pass in the '--ask-vault-pass' option:
$ ansible-playbook create_vlans.yml --ask-vault-pass
Vault password:
PLAY [Arista-Ansible Exercise1] ***********************************************
GATHERING FACTS ***************************************************************
ok: [pynet-sw1]
ok: [pynet-sw2]
ok: [pynet-sw3]
ok: [pynet-sw4]
TASK: [create VLANs] **********************************************************
ok: [pynet-sw3] => (item={'vlan_name': 'kb5', 'vlan_id': 225})
ok: [pynet-sw2] => (item={'vlan_name': 'kb5', 'vlan_id': 225})
ok: [pynet-sw1] => (item={'vlan_name': 'kb5', 'vlan_id': 225})
ok: [pynet-sw4] => (item={'vlan_name': 'kb5', 'vlan_id': 225})
PLAY RECAP ********************************************************************
pynet-sw1 : ok=2 changed=0 unreachable=0 failed=0
pynet-sw2 : ok=2 changed=0 unreachable=0 failed=0
pynet-sw3 : ok=2 changed=0 unreachable=0 failed=0
pynet-sw4 : ok=2 changed=0 unreachable=0 failed=0Note, at this point, the VLAN already exists so nothing actually changes when I execute the playbook. The playbook is connecting to the switch correctly, however.
For more information see: Encrypting content with Ansible Vault
Kirk Byers