About Us
Kirk Byers is the founder of Twin Bridges Technology–a business specializing in network automation training. He is the creator of the Netmiko Python library and also one of the core maintainers of the NAPALM project.
He teaches Python, Ansible, and Nornir courses for Network Engineers and writes about network automation at pynet.twb-tech.com. He is a long-time network engineer (CCIE #6243 emeritus), has extensive experience with *nix system administration, and is a Python programmer. He is interested in programming and networking and how to improve network engineering practices through automation.

Our Courses
Since 2014, we have offered paid courses on network automation including courses on Python, Ansible, Netmiko, and Nornir.
Open-Source Work
Since 2014, we have been contributors to various Network Automation open-source projects.
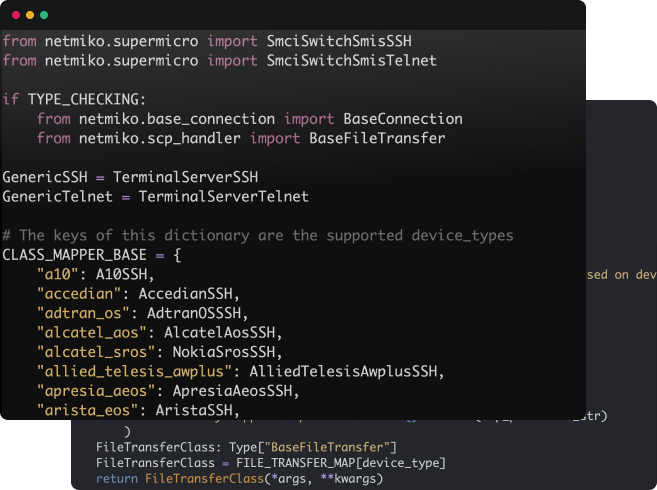
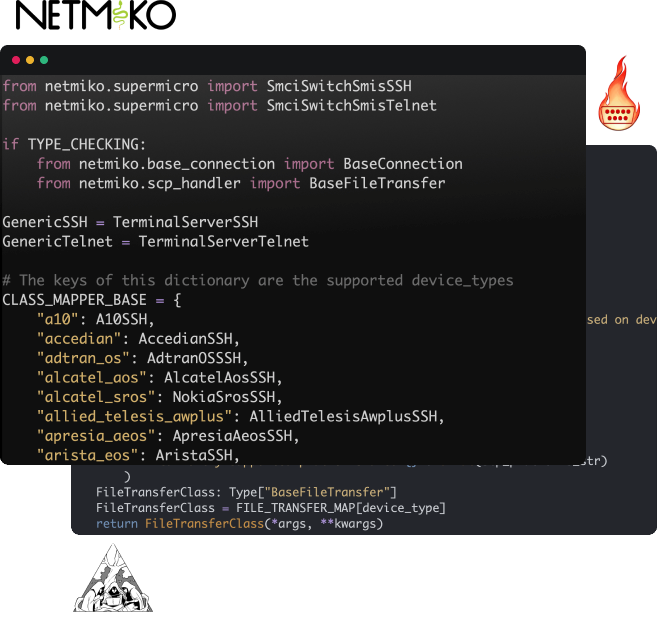
In 2014, Kirk began work on the Netmiko library which simplifies automating legacy screen-scraping. We have actively maintainted that library since that time and have increased the Netmiko driver support to over eighty vendors.
In addition, to our Netmiko work we have done extensive work on the NAPALM automation library. Kirk is one of the core NAPALM maintainers. He was a key contributor on the Cisco IOS driver for NAPALM. He also has maintained many aspects of the NAPALM NX-OS driver and the NAPALM-Ansible modules.
Twin Bridges has also worked on the Nornir Automation Framework including maintaining the nornir-netmiko bindings and helping with several other Nornir plugins.
Student Success
-

I highly recommend both courses (Ansible and Netmiko) for those looking to learn more about network automation. Kirk Byers does a great job at explaining the content, provides the lab resources required to perform the course material, and is good at responding to questions on his Slack Channel.
Andrew Turner -

I have taken several paid and non-paid Python courses. I can say that by far your course is the best one I have taken. The way you explained stuff just makes sense to me.
Joli MartinezAutomation Engineer -

I am on the material for the 3rd week and I just wanted to compliment you on the way that you explained how to unwrap the data structures. Best step by step explanation I have seen so far to help me understand and work with the data. Thank you very much!
Ray deGuzmanSenior Network Engineer