Netmiko Library
Since late 2014, I have been working on an open-source Python library that simplifies SSH management to network devices. The library is based on the Paramiko SSH library and is named Netmiko.
You can find the library at https://github.com/ktbyers/netmiko and the latest released version of the software can be installed using pip.

Library Purpose
The purposes of this library are the following:
- Successfully establish an SSH connection to the device.
- Simplify the execution, retrieval, and formatting of show commands.
- Simplify the execution of configuration commands.
- Abstract away much of the low-level mechanics of interacting with devices.
- Provide a (relatively) uniform API for interacting with devices.
- Do the above across a broad set of networking vendors and platforms.
Supported Platforms
Netmiko currently supports about eighty different platforms.
For a mostly complete list of supported platforms see PLATFORMS.md.
In addition to SSH support, Netmiko also supports Secure Copy, telnet connections, and serial connections. The platform support for each of these is more limited than SSH. Once again see the PLATFORMS.md file for more details on the platforms supported for these use cases.
Getting Started
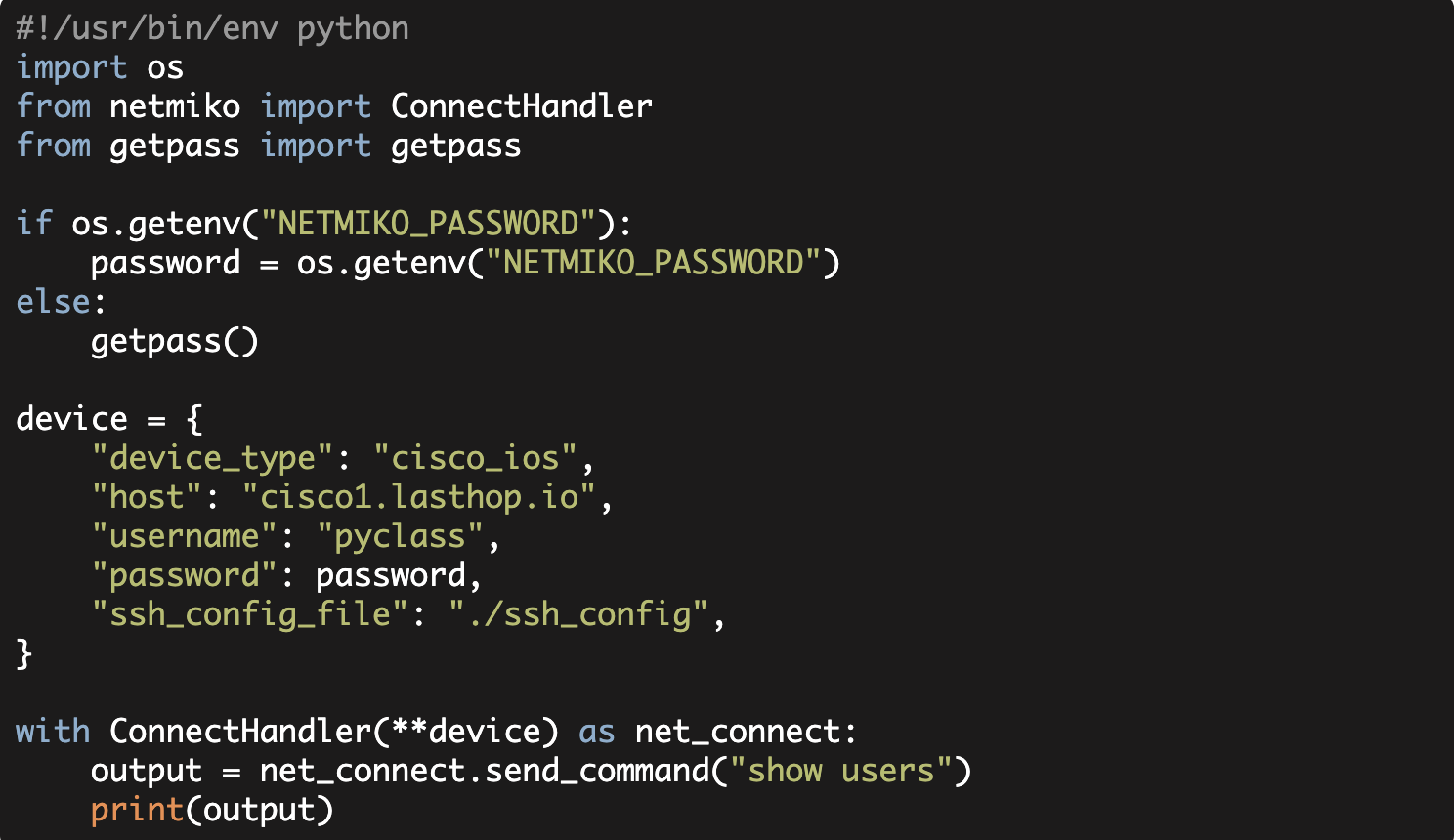
Import "ConnectHandler" from the Netmiko library. You can think of ConnectHandler as your main entry point into the library. It picks the right class for you, creates a Netmiko object based on that class, and establishes an SSH connection to the remote device.
from netmiko import ConnectHandlerYou would then use ConnectHandler to pick the class and establish the SSH connection.
This requires us to pass in certain arguments namely our:
- device_type
- host (hostname or IP)
- username
- password
Netmiko's available device types are once again listed in the PLATFORMS.md file.
net_connect = ConnectHandler(
device_type="cisco_xe",
host="cisco5.domain.com",
username="admin",
password="password",
)At this point the variable 'net_connect' should be a usable SSH connection to the remote device.
>>> net_connect
<netmiko.cisco.cisco_ios.CiscoIosSSH object at 0x7f3403b16fd0>
>>> net_connect.find_prompt()
'cisco5#'Executing Show Commands
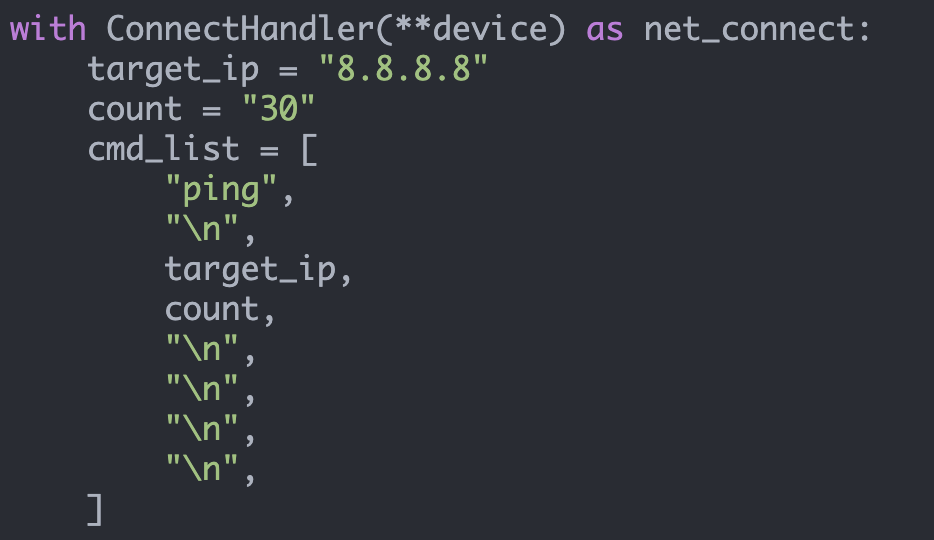
One of the next things that you probably want to do is retrieve show command output from your device. This can be accomplished by using the 'send_command()' method.
>>> output = net_connect.send_command("show ip arp")
>>> print(output)
Protocol Address Age (min) Hardware Addr Type Interface
Internet 10.0.2.2 57 5255.0a00.0202 ARPA GigabitEthernet1
Internet 10.0.2.3 116 5255.0a00.0203 ARPA GigabitEthernet1
Internet 10.0.2.15 - 5254.0012.3456 ARPA GigabitEthernet1Notice that Netmiko automatically processes the output and strips the command echo. Additionally, it strips the trailing router prompt. In other words, it attempts to leave you with only the show command output and nothing else.
Also you should not have to disable output paging. Netmiko should do this automatically when it connects to the device.
Our complete script at this point would be the following:
from netmiko import ConnectHandler
net_connect = ConnectHandler(
device_type="cisco_xe",
host="cisco5.domain.com",
username="admin",
password="password",
)
output = net_connect.send_command(
"show ip arp"
)
print(output) And execution of this script would print the following:
$ python show_command.py
Protocol Address Age (min) Hardware Addr Type Interface
Internet 10.0.2.2 64 5255.0a00.0202 ARPA GigabitEthernet1
Internet 10.0.2.3 123 5255.0a00.0203 ARPA GigabitEthernet1
Internet 10.0.2.15 - 5254.0012.3456 ARPA GigabitEthernet1Making Configuration Changes
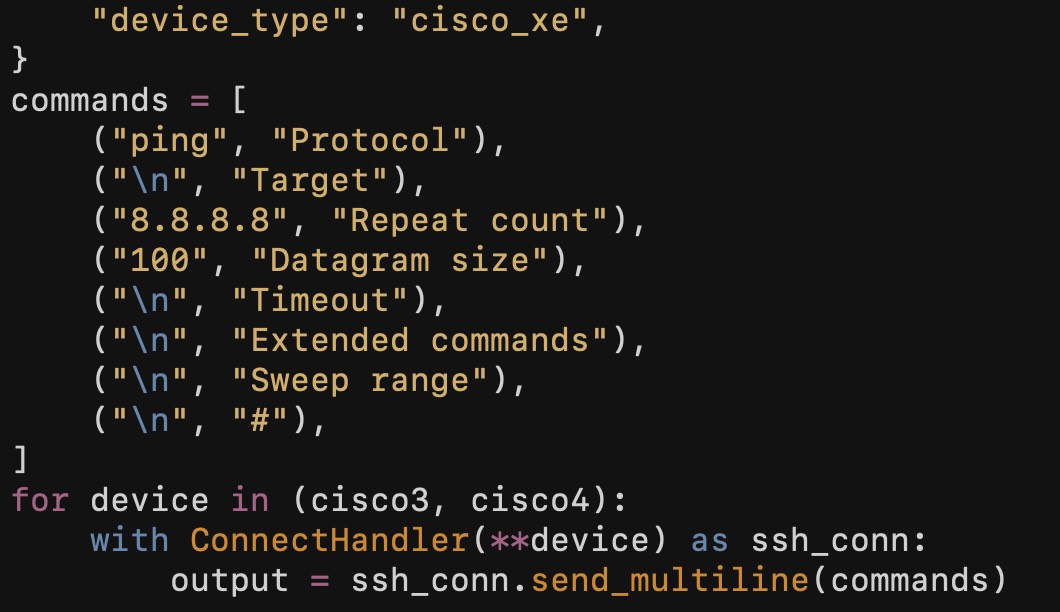
Before too long, you will probably want to make some configuration changes using Netmiko. You can accomplish this using Netmiko's send_config_set() method.
cfg_list = [
"ip access-list extended TEST1",
"permit ip any host 1.1.1.1",
"permit ip any host 1.1.1.2",
"permit ip any host 1.1.1.3",
"permit ip any host 1.1.1.4",
"permit ip any host 1.1.1.5",
]
cfg_output = net_connect.send_config_set(cfg_list)
print(cfg_output)Here I create a list of configuration commands and then provide that list to the 'send_config_set()' method.
The 'cfg_output' variable will show me what occurred during that SSH session. Once again, Netmiko will do a set of things automatically—in particular, it will both enter and exit configuration mode (if necessary).
You can then save your running-config to startup-config by executing the 'save_config()' method.
net_connect.save_config()Additional Articles
Of course, there is a lot more that you can do using Netmiko. I have written articles about a set of these features across time.
I have also written the following article describing some of the characteristics of how Netmiko deteremines when a command is done. Note, this article mostly pertains to Netmiko 3.X and does not really apply to Netmiko 4.X or later.
Finally, I have a set of articles detailing new features in Netmiko 4.X. Netmiko 4.X should come out in the fall of 2021.
Netmiko's Command-Line Tools
Netmiko has a set of command-line tools. For more details on these tools see the following articles.
Additional Examples
There are lots of additional examples here.
Additional Documentation
Kirk Byers